Тaking control
In "The tools of the trade" we saw the basics of working with FreeBSD. In this part of the book, we'll look at some more system-specific issues. This chapter discusses the following topics:
- UNIX is a multi-user operating system. We've already skimmed over creating user accounts, but on page 144 we'll look at it in more detail.
- Not all users are created equal. In particular, the system administration login root has power overall other users. We'll look at root on page 146.
- UNIX implements multi-tasking via a mechanism called processes. We’ll look at them on page 148.
- Timekeeping is extremely important in a networking system. If your system has the wrong time, it can cause all sorts of strange effects. On page 155 we'll look at how to ensure that your system is running the correct time.
- A number of events are of interest in keeping a machine running smoothly. The system can help by keeping track of what happens. One mechanism for this is log files files that contain information about what has happened on the machine. We'll look at them on page 157.
- On page 159, we'll look at how FreeBSD handles systems with more than one processor. This is also called Symmetrical Multi-Processor or SMP support.
- Nearly every modern laptop has as special bus for plugin cards. It used to be called PCMCIA an acronym for the rather unlikely name Personal Computer Memory Card International Association. Nowadays it's called PC Card. It was later upgraded to a 32 bit bus called CardSus We'll look at how FreeBSD supports PC Card and CardBus on page 159.
- Starting on page 162, we'll look at FreeBSD's support for emulating other operating systems.
- Other aspects of FreeBSD are so extensive that we'll dedicate separate chapters to them. We'll look at them in "The Ports Collection" to 15.
- Starting and stopping the system is straightforward, but there are a surprising number of options. Many of them are related to networking, so "Starting and stopping the system" is located after the networking section.
Users and groups
We've already looked at users in "The tools of the trade" . In this chapter, well take a deeper look.
In traditional UNIX, information about users was kept in the file /etc/passwd. As the name suggests, it included the passwords, which were stored in encrypted form. Any user could read this file, but the encryption was strong enough that it wasn't practical to decrypt the passwords. Nowadays processors are much faster, and it's too easy to crack a password. As a result, FreeBSD keeps the real information in a file called /etc/mas-ter.passwd, and for performance reasons it also makes it available in database form in /etc/pwd.db and /etc/spwd.db. None of these file are user-readable. /etc/passwd remains for compatibility reasons: some third-party programs access it directly to get information about the environment in which they are running.
Choosing a user name
So what user name do you choose? User names are usually related to your real name and can be up to eight characters long. Like file names, they're case-sensitive. By convention, they are in all lower case, even when they represent real names. Typical ways to form a user name are:
- First name. In my personal case, this would begreg.
- Last name lehey
- First name and initial of last name gregl
- Initial of first name, and last name glehey
- Initials gpl
- Nickname (for example, grog)
I choose the last possibility, as we will see in the following discussion.
Adding users
We've already seen how to use sysinstall to create a user. It's not the only way. There are at least two other methods. One is the program adduser:
# adduser Use option "-verbose" if you want see more warnings & questions or try to repair bugs. Enter username [a-z0-9]: yana Enter full name []: Yana Lehey Enter shell bash csh date no sh [bash]: accept the default Uid [1000]: accept the default Enter login class: default []: accept the default Login group yana [yana]: home Login group is "home". Invite yana into other groups: no [no]: wheel to be able to use su Enter password []: no echo Enter password again []: no echo Name: yana Password: **** Fullname: Yana Lehey Uid: 1000 Gid: 1001 (home) Class: Groups: home wheel HOME: /home/yana Shell: /bin/bash OK? (y/n) [y]: accept the default Added user "yana" Add another user? (y/n) [y]: n
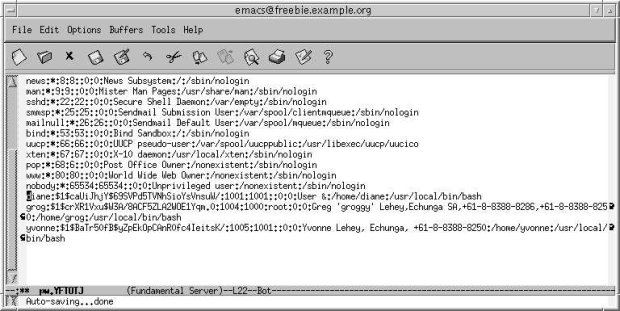
An alternative way of adding or removing users is with the vipw program. This is a more typical UNIX-hackish approach: vipw starts your favorite editor and allows you to edit the contents of the file /etc/master.passwd. After you have finished; it checks the contents and rebuilds the password database. Figure 8-1 shows an example.
You might be wondering why would you ever want to do things this way, and you might find it funny that most experienced UNIX administrators prefer it. The reason is that you get more of an overview than with a peephole approach that graphical environments give you, but of course you need to understand the format better. It's less confusing once you know that each line represents a single user, that the lines are divided into fields (which may be empty), and that each field is separated from the next by a colon (:). Table 8-1 describes the fields you see on the line on which the cursor is positioned. You can read more about the format of /etc/master.passwd in the man page passwd(5).
| Field | Meaning |
|---|---|
| yvonne | User name. |
| (gibberish) | Encrypted password. When adding a new user, leave this field empty and add it later with the passwd program. |
| 1005 | User number. |
| 1001 | Group number. |
| (empty) | Login class, which describes a number of parameters for the user. We’ll look at it in "Starting and stopping the system" , on page 571. This field is not included in /etc/passwd |
| 0 | Password change time. If non-0, it is the time in seconds after which the password must be changed. This field is not included in /etc/passwd. |
| 0 | Account expiration time. If non-0, it is the time in seconds after which the user expires. This field is not included in /etc/passwd. |
| Yvonne Lehey | The so-called gecos field, which describes the user. This field is used by a number of programs, in particular mail readers, to extract the real name of the user. |
| /home/yvonne | The name of the home directory. |
| /bin/bash | The shell to be started when the user logs in. |
The super user
FreeBSD has a number of privileged users for various administration functions. Some are just present to be the owners of particular files, while others, such as daemon and uucp, exist to run particular programs. One user stands above all others, however: root may do just about anything. The kernel gives root special privileges, and you need to become root to perform a number of functions, including adding other users. Make sure root has a password if there is any chance that other people can access your system (this is a must if you have any kind of dialup access). Apart from that, root is a user like any other, but to quote the man page su(1):
By default (unless the prompt is reset by a startup file) the super user prompt is set to # to remind one of its awesome power.